One of the most pressing questions all business owners have been asking themselves since lockdown began is ‘How secure is it for my team to work remotely?’ and ‘What practices do I need to put in place to make secure remote working possible?’
Since being introduced to the cloud, many business owners are embracing the benefits of running applications on a scalable platform without needing to run them in a private data centre in the office. However, unlike a centralised team which can be put on lockdown if there is a breach of security, remote working teams have a far larger attack surface, making information systems subject to identity theft. With the right set of policies in place, you can minimise the risk of a security breach.
Having a Business Contingency Plan in place is one of the very first steps when sending your employees home making sure all security information is shared between teams, including having passwords, codes, security management listings and tech support information to hand at all times.
Taking the necessary measures to enforce information security and protect your information systems from unauthorised access, use, disclosure, disruption, modification or destruction is paramount for any remote working policy. This article will take you through some of the best security practices to protect your data, confidential information and ensure your systems overall integrity.
Use a Secure Internet Connection
Take the reasonable precautions to ensure that your internet connection is private and that no one unauthorised has access to your internet connection outside of your home. You can do this by using a WPA2 to password protect your own personal WiFi and have your VPN (Virtual Private Network) Proxy turned on at all times. This will protect and encrypt your data regardless of the network settings.
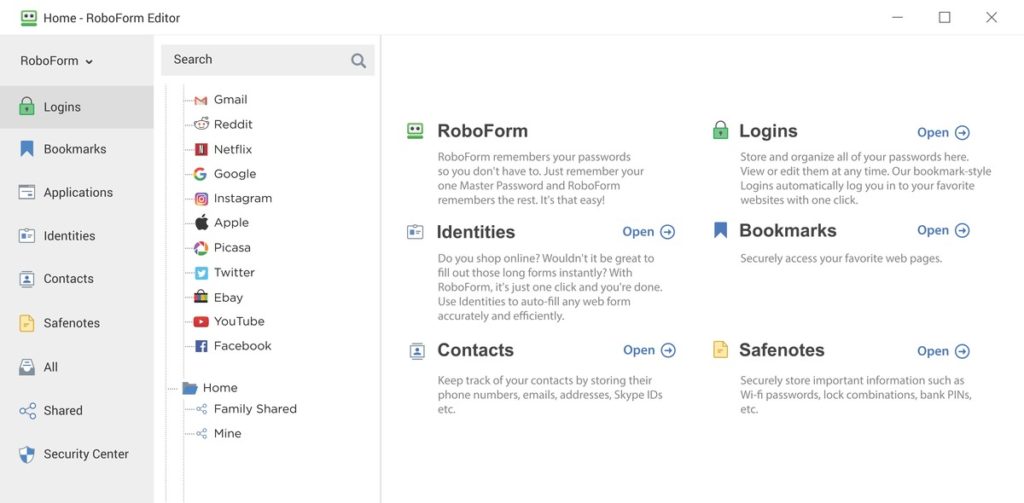
Create a Password Management System
Every organisation must run a password audit designed to ask for access to the company’s services for security purposes. You can ask your employees to provide the toughest protection across all devices and ensure all business-related passwords are stored securely.
Using a password management system like RoboForm will further ensure that all your passwords are kept securely in one place and can be accessed remotely. A password manager is the best way to ensure your remote working team is meeting the standards for secure passwords, storing them in an encrypted database and retrieving them when needed. They can also be shared with others without compromising account security.
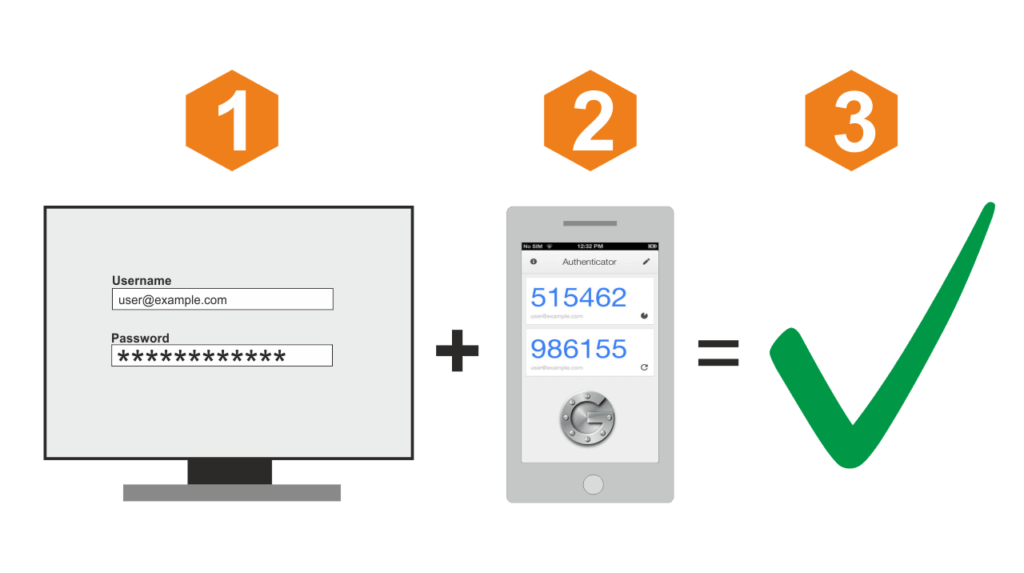
Use Two-Factor Authentication
Two-Step Authentication is more secure than just using One-Factor Authentication. MFA is a secure access control procedure required to establish strong checkpoints that mitigate potential threats. MFA for any organisation will require a second ID factor used to validate the user’s identity which is often a code sent to the user’s smartphone.
The multi-factor combination involves several credentials including something the user knows, such as a password, Personal Identification Number (PIN) or the answer to a security question, something the user has like a device and/or something the user is, like a fingerprint or voice recognition.
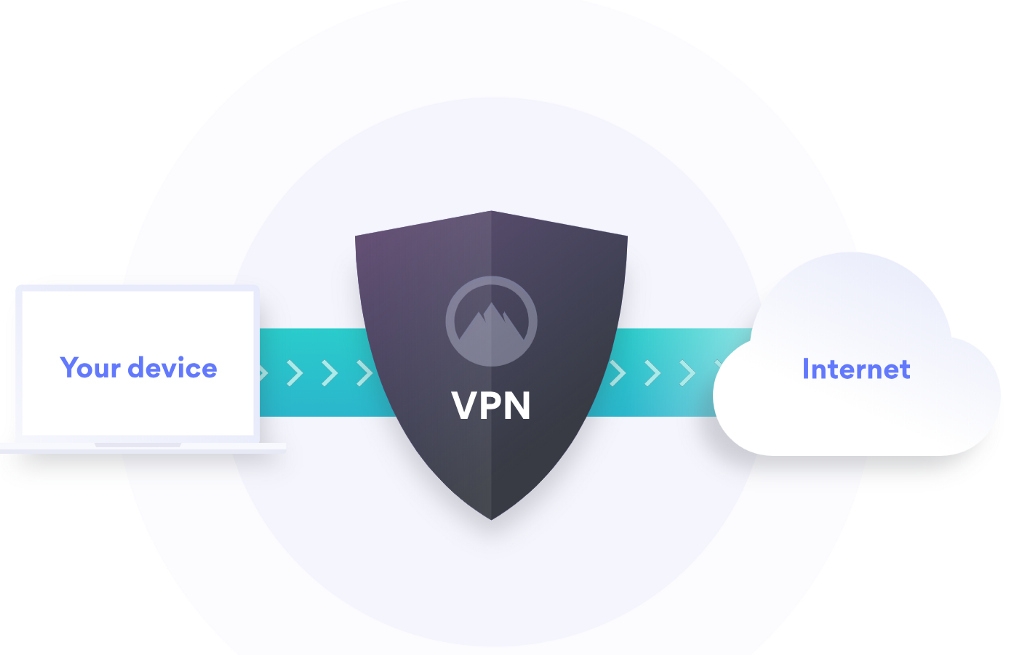
Provide VPN Access
One of the best ways of improving security practices for remote workers is to provide them with access to a VPN network. This provides an additional layer of security moving between the external systems and devices that your employees are using and your main in-house system. It offers elements such as masking the user’s location, hiding the user’s IP address and encrypting data transfers during the transit.
A VPN network creates an encrypted tunnel between a user’s computer or mobile device and a server connected to the internet. This means that no one between the user and the server can gain access to the data that is being transmitted while the VPN is on offering protection against security breaches.
Invest in File Sharing Software
File sharing mobilises all of your important documents and files via the cloud and syncs them across all devices and teams. Investing in a platform like Google Cloud, to store all of your files and access them remotely is highly recommended as part of your remote working practices.
Other common file-sharing platforms are Dropbox, Microsoft OneDrive and Hightail allowing you to sync your files across multiple devices and collaborate with other teams with ease. Keeping all your work files in one accessible location minimises the risk of having your systems intercepted by an unwanted third party.

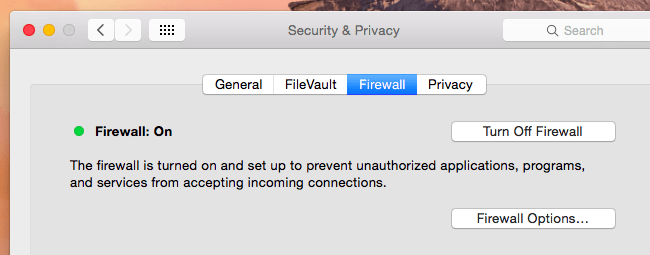
Turn on Your Firewall
A firewall controls all network traffic to and from your computer and is designed to prevent unauthorised access to or from a private network. It works explicitly by asking you whether to allow new programs to access your network. You can turn on your firewall in the settings menu to prevent unauthorised applications, programs and services from accessing your server.
Firstly you will need to create an administrator to manage the firewall, delete, disable or rename any default user accounts and change all default passwords. Then you will need to disable simple network management protocol (snmp) or configure it as a secure community string and plan out your network structure. The more zones that you create to allow limited inbound traffic from the internet, the more secure your network will be.
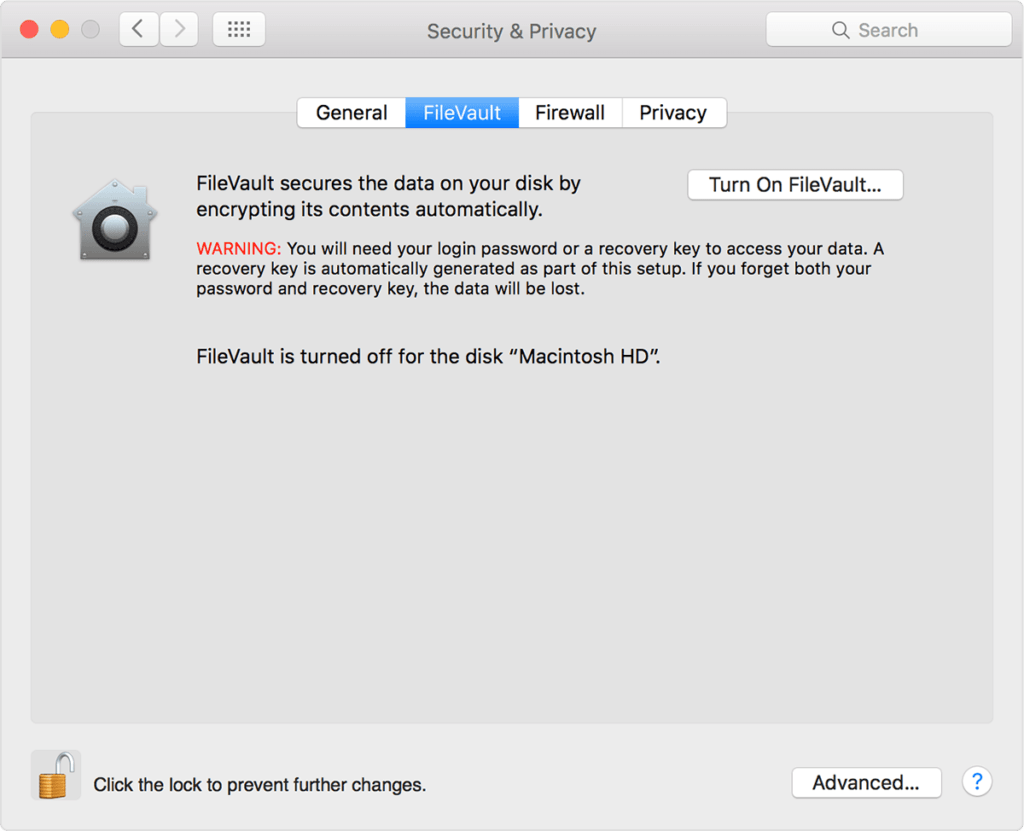
Full Disk Encryption
Full disk encryption can be turned on using FileVault on a Mac and will ensure that your entire disk’s content is inaccessible without a password, in the event that your laptop is lost or stolen. This is a cryptographic method that applies encryption to the entire hard drive including data, files, the operating system and software systems.
On a MacOS system, FileVault is the official built-in disk encryption feature which can encrypt all of the files located on the drive using 128-bit AES encryption with a 256-bit key. Any new or changed data will be automatically locked down and password protected to prevent unauthorised access.
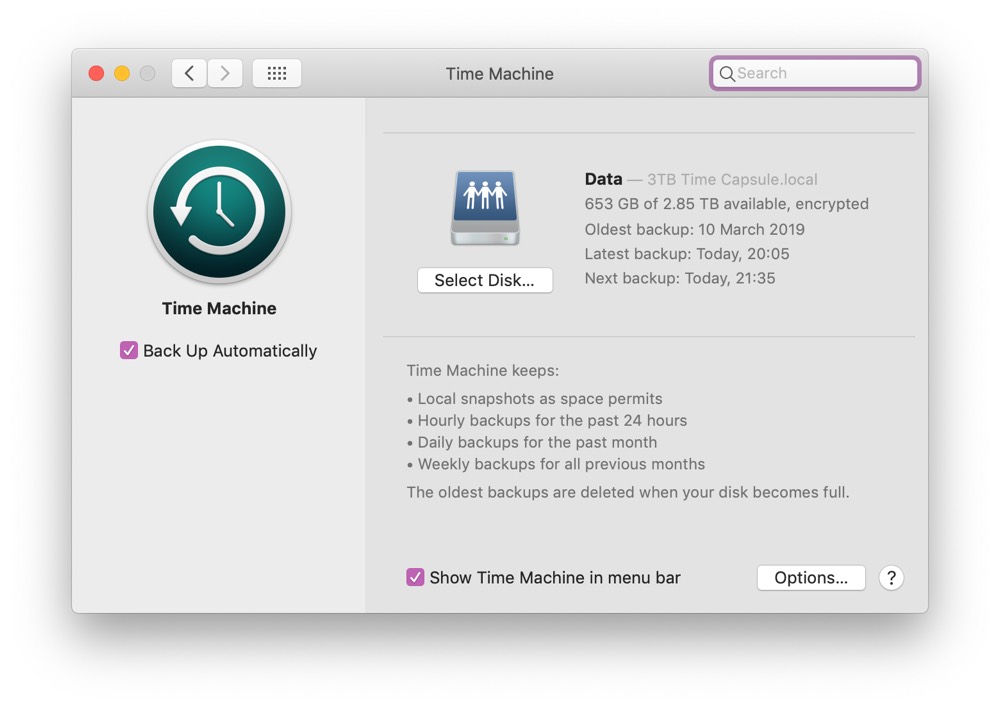
Encrypt Your Backups
In the event that your hardware might fail, or a virus infects your PC, ensure that all your backups are encrypted to protect the safety of your data. On a Mac, in the system preferences menu, select the ‘Time Machine’ option and opt to ‘Back Up Automatically’ which will complete hourly backups of your systems data.
If the backup is encrypted then it is safe for all users and administrators that know the network disk password. Anyone that knows the password will be able to access any data backed up to the disk. Device level encryption scrambles data on phones, tablets, computers and laptops protecting them in the event of a security breach. To unscramble the data you will need to decrypt it with a decryption key.
Conclusion
Utilising technology and software to help your team perform at its peak and ensuring a reliable, secure and well-equipped infrastructure is the foundation of effective remote working practices. By providing your employees with the basic knowledge of effective security practices to adhere to while remote working and encouraging safe working, you will be fully prepared to adopt a working from home structure for your teams.
At Coderus we have recently developed a Business Contingency Plan strategy to ensure that our remote working team has adopted the best security practices, keeping our network safe, secure and protected at all times. Want to find out more about remote working? Check out our latest insights blog here.























