The IoT market is set to experience significant growth in the coming years, with the number of devices expected to jump from 13.8 billion in 2021 to 30.9 billion by 2025.
The ability of IoT devices to connect to networks and transfer data makes them especially vulnerable to cyberattacks. As the Internet of Things develops and expands, the need for improved safety and security measures grows.
This article discusses everything you need to know about the problems and solutions involved with IoT devices and covers the following topics:
- What is IoT security?
- Is the IoT secure?
- Why does IoT require security?
- Why should businesses care about the risks associated with an IoT system?
- Understanding IoT Security Risks
- IoT Security Problems: What are the biggest IoT security risks and challenges?
- Top IoT Security Solutions
- IoT Security Checklists
What is IoT security?
IoT security refers to the protection of IoT devices and the networks they connect to, through several different methods, techniques, strategies and tools.
Some key IoT security methodologies include application program interface (API) security, public key infrastructure (PKI) authentication and network security.
IoT security encompasses any network that devices connect to such as Bluetooth or LoRaWAN, not just internet-based connectivity.
Is IoT Secure?
Many within the technology industry have questioned the security of IoT and connected devices, a valid concern when you consider the numerous data breaches that have occurred as a result of IoT devices being hacked into.
Whilst some device manufacturers take the necessary precautions to make sure the products they produce are as secure as possible, many do not, as the industry lacks adequate global legislation and guidelines to ensure security standards are held up across the board.
Until we have this in place, it would be incorrect to say that the Internet of Things is 100% secure, as each manufacturer produces devices to their own varying standards of security – some of which aren’t strong enough to protect against sophisticated cyber attacks, leaving consumers vulnerable.
Why does IoT require security?
IoT allows us to collect and analyse data for indispensable insights but for this process to be responsible, reliable and efficient, it must be carried out securely.
We need IoT security because the unique qualities that make connected devices so valuable are also what makes them open to attack.
The ability IoT devices have to connect to networks and transfer data makes them especially vulnerable to cyberattacks, giving hackers and cyber criminals the opportunity to remotely access devices, therefore robust security measures are vital.
Small-scale, common IoT devices can be hacked as part of a larger malicious strategy to gain access to entire networks.
Why should businesses care about the risks associated with an IoT system?
Not having a secure IoT system is a risk to not only users but also to your business who could be held liable. Some of the primary things you should be concerned about are:
- Customer/user data exposure: Many IoT devices collect and distribute personal information. Fitness trackers, heart rate monitors, sleep trackers, and surveillance devices all send out information that could be misused.
- Corporate/business data exposure: IoT devices, when linked directly to a company’s data centre, open security holes that are inherently beyond the knowledge of most in-house IT workers. These systems can expose the business to a high level of vulnerability and data loss.
- Physical damage: Many IoT items contain actuators that, if activated incorrectly, can cause physical harm to customers. Linked ovens and coffee makers have heating elements that could trigger a fire. Connected vehicles may be turned off in the middle of a journey or have their brakes disabled by a third party.
- Service failure and high-risk downtime: In the event that there is IoT service failure, some devices can pose fatal threats. For this reason, connected medical devices need to still function properly when offline. Not to mention, if there is unplanned downtime for an automatic pet feeder, it could endanger the life of a pet.
- Life, legal and property liability: As previously mentioned, IoT hacks can result in not only liability for data loss and identity theft, but at the same time can create existential life and property liability. Companies manufacturing connected devices are now more responsible than ever for this.
- Reputation and brand damage: In the aftermath of a security breach, companies with a strong brand could suffer financially. Consumers now have a greater voice and influence thanks to a plethora of online and offline sources available to them. Every large-scale news incident that harms a company’s image must be avoided at all cost. More importantly though, businesses need to put their users first and protect them to the best of their ability.
Understanding IoT Security Risks
Because of the diversity of devices and sheer scale of the modern IoT, a one-size-fits-all approach can not be taken with understanding and mitigating IoT security challenges and risks, instead, a bespoke solution must be developed to offer protection for any IoT deployment.
Conducting a deep security risk assessment that identifies device, network system and user and customer backend system vulnerabilities is the first point of action for any IoT business.
The risks identified must then be given solutions that are effective for the entirety of the IoT deployment life cycle, including as it scales and expands geographically.
Each layer of the IoT ecosystem has different characteristics which in turn present unique security risks that make them potential targets, these are explained in the image below.
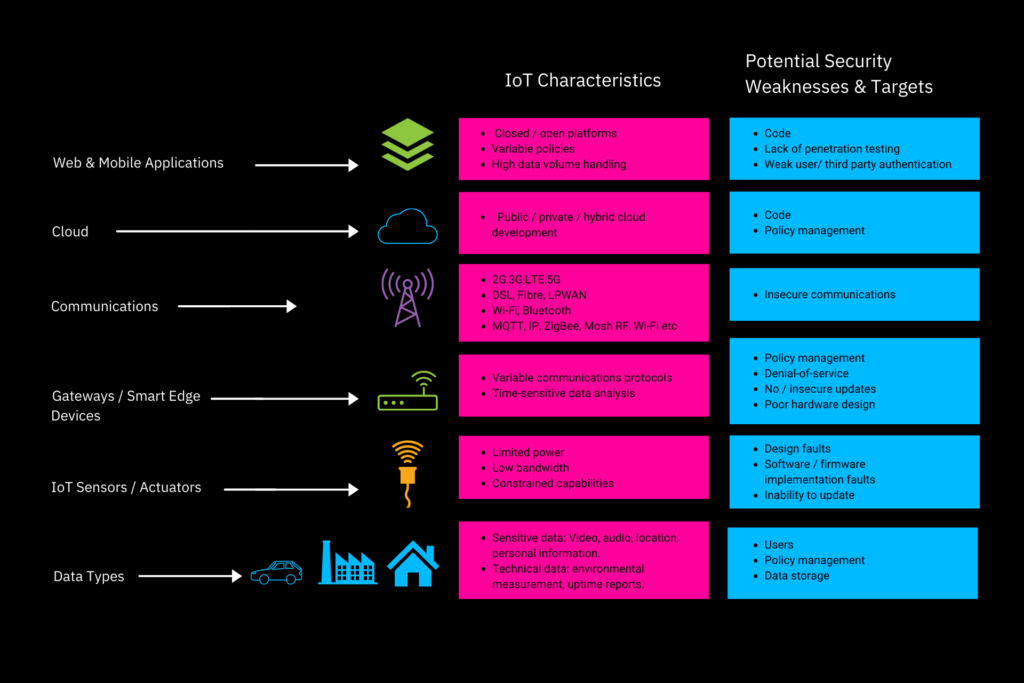
IoT Security Problems: What are the biggest IoT security risks and challenges?
The top 10 biggest IoT security concerns include:
- IoT Manufacturer Compliance Issues
- Lack of User Knowledge and Understanding
- Insecure Device Update Management
- Lack of Physical Security
- Botnet Attacks
- Industrial Sabotage
- Access to Sensitive Data
- Reduced Data Integrity
- Location Exposure
- Limited Industry Experience
Read further for more information on these IoT security problems and why they are a challenge and risk for the IoT industry.
IoT Manufacturer Compliance Issues
As a result of the IoT industry’s lack of universal security standards, manufacturers are constantly releasing new IoT devices without first ensuring that all vulnerabilities have been discovered and mitigated.
Without adequate global guidelines and codes of practice, manufacturers aren’t required to keep security at the forefront of their product design processes, meaning devices are being released to the public without strong IoT security solutions.
Some of the main manufacturer security risks associated with IoT devices are:
- Weak, easily guessed, or hard-coded passwords
- Hardware issues
- Insecure update mechanisms
- Embedded operating systems and software that’s outdated or unpatched
- Lack of secure data management, transfer and storage facilities
Lack of User Knowledge and Understanding
Whilst we’ve identified that a majority of IoT security problems begin with the manufacturers’ faults and lack of proper risk assessments, a lot of issues are caused by the fact that end-users don’t properly understand the technology and end up creating further threats.
Most people are now aware of the value of securing their Wi-Fi networks with strong passwords, performing regular virus scans on their computers and other routing cybersecurity practices.
However, greater education and raised awareness of the risks associated with IoT devices is required to overcome the challenges presented by user ignorance or lack of knowledge, which would make IoT device usage safer and more secure.
Insecure Device Update Management
A manufacturer will sell a device to consumers with the latest software available, however, over time new vulnerabilities will arise for cybercriminals to identify and exploit, meaning a device that was considered secure at the point it was sold will become more and more insecure as time goes on.
This is why routine updates and maintenance are key to ensuring the longevity of IoT device security. Unfortunately, some manufacturers are more focused on producing and delivering new devices to market as quickly as possible rather than giving the security of older devices the attention they demand so only offer updates for a limited time or in some cases, not at all.
However, updates must be carried out properly or further risks could be created. A device will experience a short downtime during an update whilst it sends a backup to the cloud, if this connection is unencrypted and the updated files aren’t protected, hackers and cybercriminals would be able to access and steal sensitive data.
Another issue is that many IoT products are still able to be used normally without the necessary updates being carried out, unlike the automatic updates we see on our smartphones, tablets and computers for example.
Lack of Physical Security
Often, when consumers do consider protecting their IoT devices they fail to think of physical threats as well as non-physical ones. To be fully secure, all devices need to be protected from physical, external threats such as USB flash drives with Malware – devices that are placed in remote locations for extended periods are especially vulnerable to this kind of attack.
This responsibility begins with manufacturers, however, the difficulty they face lies in building secure sensors and transmitters for cost-effective devices.
The responsibility then extends to users who should ensure their IoT devices such as smart motion sensors or security video cameras are as physically secure as possible to remove the opportunity for them to be tampered with.
Botnet Attacks
A botnet is a large network of infected IoT devices cyber criminals build to use for targeted attacks by directing them to send thousands of requests per second to bring down a specified target.
Unfortunately, IoT devices are incredibly vulnerable to Malware attacks due to their insecurity so they can quickly and easily be turned into bots.
Botnets are used for several different types of attacks but are mostly associated with DDoS (Distributed Denial of Service) attacks.
A DDoS attack is when a cybercriminal uses the botnet to inundate the server, computer, or network that is being targeted with a constant stream of network requests. The target becomes unable to handle all of the requests, crashes and is rendered unavailable for users. This outage can last as long as 24 hours in some cases.
On the other end of the spectrum, it’s also key for businesses within the IoT industry to pay attention to smaller-scale attacks, which can be subtle and small enough to perform microbreaches without being detected.
Industrial Sabotage
When an IoT device is hacked into, the hacker will gain access to its data and control of its functions and depending on the type of IoT device being hacked into, there’s potential for a huge amount of damage to be done.
If an office coffee machine was hacked into, it’s unlikely the hacker would be able to do much more damage than seeing how many lattes had been made that day and making one for themselves.
However, if they were to target businesses in the manufacturing and supply chain industry and hack into a factory’s machinery, they could cause massive safety issues, halt production for a set period or indefinitely. The cybercriminal could then effectively hold the machinery ransom until the business pays the fee demanded for the release of their machinery.
Access to Sensitive Data
Businesses large and small alike are responsible for ensuring that the sensitive data they collect and store is protected, for theirs and their customers’ safety.
Usually, businesses address this by implementing security measures that protect the databases this information is stored in, but neglect to consider other potential access points for cybercriminals such as printers.
A printer that has been compromised could give a hacker the ability to see everything that the office prints or scans – which is likely to contain sensitive information that can be used maliciously.
The same can be said for wearables, health equipment, smart toys and many more IoT devices.
Reduced Data Integrity
Data is always being transmitted to and from IoT devices before being stored and processed. Sometimes, data is transmitted without any encryption so a hacker can intercept this stream and alter the data being sent.
In the healthcare industry, this could be potentially life-threatening if false signals were sent regarding a patient’s state of health, as doctors might perform procedures that could cause detriment to their health or even cause them further harm.
In one case, a medical device manufacturer released an implantable cardiac device with vulnerabilities that meant a hacker could gain control of the pacemaker to deplete the battery to alter the pacing or shocks.
Location Exposure
Due to the rising trend of automation and smart homes, most residences and businesses host large numbers of IoT devices, which poses a substantial threat to physical security, not just cybersecurity.
Insecure IoT devices can be used to expose a home or business’s IP address which can then be used to identify its address. This sensitive information can then be sold by the hacker who obtained it to whoever they choose.
Limited Industry Experience
Because of the relative youth of IoT as an industry, professionals in this industry have limited access to background information on historic threats, vulnerabilities and failures in protection.
Until more cybersecurity experts begin to specialise in the field of IoT, few basic guidelines and industry standards are available.
Top IoT Security Solutions
While there are many IoT security problems, there are also solutions that can be implemented, which we expand on below, such as:
- IoT API Security Methods
- IoT App Security
- IoT Network Security
- Authentication Mechanisms
- IoT Data Encryption
- IoT PKI Security
- IoT Security Analytics
IoT API Security Methods
Using IoT API security methodologies can not only protect the integrity of data collection and transmission between devices, back-end systems and applications using documented REST-based APIs.
As well as this, this solution ensures that only authorised devices, developers and apps are communicating with APIs or identifying potential risks or attacks against specific APIs.
IoT App Security
Before the app development process begins, developers must complete a full risk assessment and research the most appropriate security measures then devise a plan to balance app security with UI.
The relevant security technologies identified must then be implemented to mitigate the potential vulnerabilities discovered during the risk assessment process.
IoT Network Security
Utilise traditional endpoint security features such as antivirus, anti-malware, firewalls and intrusion detection technologies to ensure the protection and security of the networks that connect IoT devices to back-end systems.
Authentication Mechanisms
Device manufacturers should give users the ability to authenticate their IoT devices with multiple user management features for a single IoT device (such as a connected car), two-factor authentication, digital certificates and biometrics.
IoT Data Encryption
Using cryptographic algorithms to encrypt the data collected by IoT devices and communicated to back-end systems can help maintain data integrity and prevent hacking attempts.
Because of the way IoT devices and hardware profiles vary, it’s not possible to have a standard encryption process and protocols so a bespoke approach should be taken for each case.
IoT PKI Security
Use IoT public key infrastructure to ensure the connection between IoT devices and apps is secure. This method could include X.509 digital certificates, cryptographic keys and life-cycle capabilities including public/private key generation, distribution, management and revocation.
IoT Security Analytics
Through the collection, monitoring and management of data from IoT devices, actionable reports and alerts can be generated on specific activities or activities that do not align with the established policies.
With IoT security analytics, complex machine learning, AI and big data techniques are used for more predictive modelling and anomaly detection, helping to detect IoT specific attacks and threats that can’t be exposed using traditional network security tools such as firewalls.
IoT Security Checklist
As outlined earlier on in this article, IoT security problems can arise with both manufacturers and users, however, there are a number of practices that both parties can complete to improve the security of their IoT devices.
Checklist for IoT Device Manufacturers
What are some ways device manufacturers can secure their IoT systems and devices?
- Secure devices by default: Don’t rely on your customers to have the knowledge and understanding to secure their devices themselves, take the necessary precautions to provide the highest level of security possible without the user having to take any action. Ensure all messages sent are encrypted and secure.
- Repeatedly conduct penetration testing: Stay ahead of the latest hacking techniques by consistently testing systems and devices with security researchers before fixing potential vulnerabilities that have developed.
- Utilise hardware keys: Give each device its own private hardware key – this will ensure unauthorised hardware can’t access devices.
- Provide regular firmware updates: You should design a robust update strategy for any vulnerabilities that arise throughout the life cycle of the device.
- Assume source code visibility: Ensure the device has no hard-coded secrets that can impact security for all devices that hackers can use to reverse engineer. If hard-coded secrets are necessary, design them to be different for each device.
- Offer decommissioning support features: Make sure users have an easy way to remove all of their data from devices so they can be sold or disposed of safely when no longer needed.
- Find an IoT security partner: If your in-house team lacks the experience or expertise to navigate this field, research specialist agencies in IoT device security to ensure high standards.
Checklist for IoT Device Users
What are some of the ways IoT device users can secure their IoT system?
- Brands: Use known brands names with good reputations as they’re more likely to prioritise security.
- Passwords: Change default passwords when using new devices for the first time – hackers can use default passwords to access your device if you don’t change them.
- Updates: Frequently check for firmware and system updates as an update might be released to fix an identified security threats.
- Guest WiFi: Set up a guest WiFi network specifically for IoT devices, as isolating IoT devices from home computers reduces the risk of hackers being able to access sensitive data.
- Universal Plug-and-Play: Turn Universal Plug-and-Play off on your router because some devices can leave your home firewall at risk of attack via UPnP.
- Home Network Security: Regularly update your home network security, as not adjusting the settings on your home WiFi network could leave you vulnerable to basic, unsophisticated attacks.
- Encryption: Enable encryption wherever possible and consider researching and only purchasing devices that support encryption.
- WiFi Restriction: Do not allow devices to connect automatically via WiFi as this helps limit the risk of device infiltration.
- Device Functions: Turn off any device functions that aren’t needed. This could include cameras, microphones, etc.
- Device Access: Ensure the device cannot be accessed physically by external parties especially if the device is located somewhere remote.
Checklist for IoT Connected Products
This checklist covers areas to review in creating a minimal attack surface area, as well as features and actions key to maintaining a secure system in a rapidly evolving field.
- Operating Systems (OS): Any accessible protocol and open port is a potential point of attack. Each form of communication needed by a product is deliberately introduced by the product developer and code on microcontroller units (MCUs) runs “bare metal” with no supporting operating system. Many SOCs and Linux systems, on the other hand, come with several open ports by design, exposing a wide range of attack vectors that product developers might not even be aware of.
- Application Programs: On a complete system on a chip device, there can be multiple application programs running, and the more applications there are, the more bugs or security vulnerabilities there are. Running an audit and sanitising these systems is essential to the viability of your product.
- Dependencies: It’s vital to establish a robust process for verifying that your external dependencies and libraries are up to date and validated. Modern encryption and communication protocols evolve and change, and you must invest in staying up to date or risk being blind to new security flaws. A greater number of dependencies, including application stability, necessitates further maintenance.
- Device Communication: Man-in-the-middle attacks, replay attacks and the loss of confidential data are only a handful of the dangers that may emerge if communications between the system and the cloud are not encrypted, or are encrypted insecurely. Confidentiality, honesty, integrity and authenticity are all guaranteed with proper encryption.
- The Cloud: Servers that are always on and connected necessitate continuous monitoring and testing. You can reduce the risk for each cloud server by restricting the network, device and dependency surface area, as well as closely monitoring access and behaviour. For your dependencies, operating systems, and service providers, you can subscribe to security mailing lists and alerts.
- User Access and Security: Threats come in all shapes and sizes, and they could come from within your organisation. Create a positive security and awareness culture for your team, and teach them how to recognise phishing and social engineering attacks. Two-factor authentication, secure passwords and whole-disk encryption are all good ways to limit the scope of harm caused by careless user error.
If you are looking into developing an Internet of Things device and would like to partner with a company, like Coderus, who can help ensure your system is secure, then get in touch.























